Remote work has altered the way teams work across different distances. Working with teams that are scattered frequently creates new technological issues, particularly as teams require reliable methods to connect with corporate resources.
The employees now have access to workplace computers, shared applications, or central data from any location they are wor andng. The technology that is used to facilitate these connections should be secure and simple. Many companies face issues using remote access solutions that require extensive IT expertise or stretch their budgets.
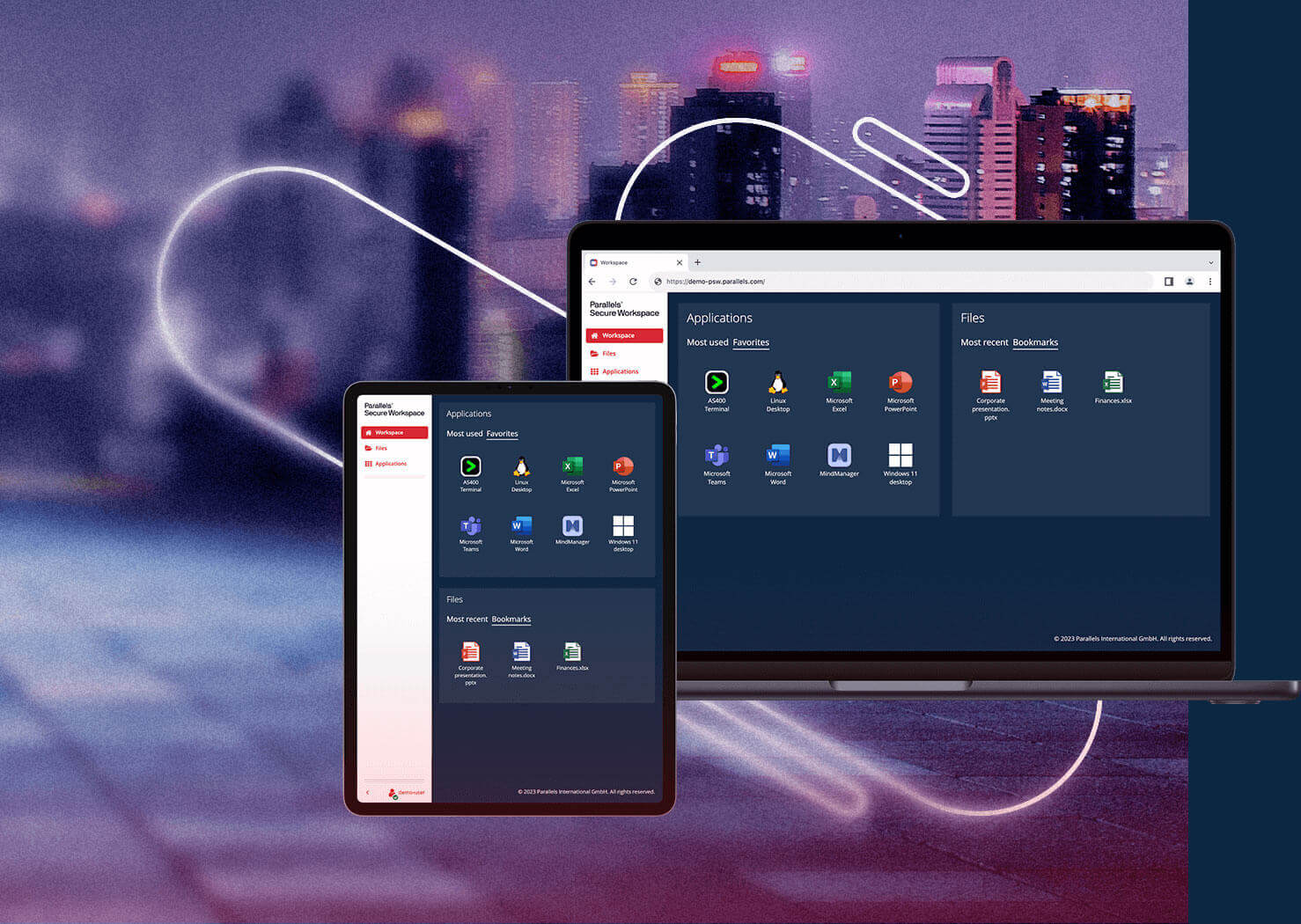
The move towards remote and hybrid working environments has led to remote desktop technology becoming increasingly essential for companies, regardless of size. Remote access software links workspaces across various places.
Small and mid-sized companies are faced with challenges when setting up remote desktop capabilities. They typically have to pick between costly solutions for an enterprise that offer many features or a basic solution that lacks the security they require.
Key Distinctions Between Remote Desktop and Remote Access
Remote desktops and remote access are sometimes misunderstood, but they address different issues. Knowing the distinctions between these two can help teams decide on the most appropriate solution to meet their requirements.
Remote desktops let users control a computer from a distance. The user can see the full screen of the machine and can operate it like he were sitting in front of it. This is ideal for server environments such as IT support or running software for office use.
Remote access encompasses a broad array of features. It could include remote desktop functions; however, it also allows users to browse the files or move them, run specific programs, or connect to network drives. This lets teams access their resources without disrupting other teams.
It is important to consider compatibility when selecting a solution. Certain products are only compatible on certain systems, for example, Windows-to-Windows connections. Others support various setups across different devices. Many businesses are considering flexible remote access solutions like TSplus because of their security and reliability.
Crucial Security Elements for Solutions Using Remote Work
Security is crucial when creating remote access. Each connection created by external connections is an entry point for cyberattacks. Cybercriminals often look for weak access points, which makes unprotected enterprises more prone to being targeted.
To minimize the risk, remote desktop applications should incorporate security components such as secure connections, multiple-factor authentication, or session tracking. Installing these features requires activating encryption in the settings of the software.
The multi-factor authentication (MFA) is an essential line of defense. It requires users to prove their identity using multiple methods before gaining access. It usually combines passwords with verification codes.
Encryption helps protect data as it travels between devices. Find remote access software that uses encryption standards such as AES-256. This makes data that is intercepted difficult to access with encryption keys.
Session monitoring tools offer administrators an online dashboard that keeps track of the users’ sessions in depth. They include the time users log in, session durations, as well as the files that are accessed and changes to the system.
Security and Usability in Balance
A secure and reliable remote access solution will fail if users are unable to solve thifto its difficulty utilize. Finding the optimal balance of security and convenience is essential to the success of your business.
Security measures directly impact user experience. Intricate password requirements, frequent prompts to sign in, and a lack of control can cause users to be fr, frustrated. But these safeguards ensure the security of sensitive company information.
Training is a crucial factor in the adoption of secure remote access. Users must be aware of what security measures are in place and how to use them in a proper manner. Training sessions that are short and focused are more efficient than long instructions.
Putting Remote Access Into Practice: A Comprehensive Guide
The successful installation of remote access requires careful planning. Start by assessing your existing infrastructure. Record what systems require remote access and who has to access them, and what security requirements are applicable.
Next, evaluate deployment options. Cloud-hosted solutions are easy to set up with no hardware requirements. On-premises solutions offer greater control, but require more expertise to manage.
Before deploying the full version, conduct thorough tests using a limited number, conducts. This can reveal potential issues with compatibility or performance. Fix these issues before the release is made available to all.
Onboarding the user is a critical aspect that is often left out of implementation plans. Create simple guides that include illustrations of the daily tasks. Plan short training sessions that focus on everyday workflows, not technical specifics.
Assessing the Success of Remote Access
After installing the Remote Desktop software, testing the effectiveness of the program can help justify the investment as well as reveal areas of improvement. A number of performance indicators could give useful information.
Connectivity reliability is usually considered to be one of the most crucial measures. Find out how frequently users experience connectivity issues or performance problems. Determine a percentage of uptime you want to achieve and then observe how closely your solution is in line with this.
The level of satisfaction with the user directly impacts productivity. Surveys can be used to collect feedback or casual conversations. Ask questions specifically about the accessibility, speed, and adequacy.
Common technical issues can be issues with printing, slow performance, and difficulties accessing certain applications,s. If users complain of lags or drops in connection, verify the capacity of your network and check bandwidth availability.
If employees are not able to access specific applications, verify permissions, and look for firewall restrictions. Make sure to test changes following each step, so that any problems are resolved properly and patterns are discovered for swift actions.
Remote work is revolutionizing the way businesses run. With the right technology for remote access, distributed teams are able to work effectively together regardless of their location. Reading reviews from independent sources can be helpful when comparing various remote desktop software.
A careful selection and constant monitoring of your system creates an experience that is smooth and supports productivity while also ensuring security.